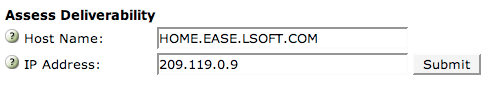


| Tech Tip (LISTSERV) – Issue 4 – 2006 Q: How can I assess my LISTSERV list deliverability infrastructure? Answer by Liam Kelly Recent increases in the amount of spam on the Internet have resulted in a tightening of anti-spam countermeasures at most email service providers. Unfortunately, the collateral damage is that a greater volume of legitimate email is being caught in those filters. This is particularly true for senders who haven't taken full advantage of the simple deliverability-protection methods already available to them. LISTSERV 15.0 includes a Deliverability Assessment to help site administrators identify possible deliverability problems before they even start sending email. In this Tech Tip, we'll discuss the Deliverability Assessment to explore basic steps that every email administrator can take to ensure that LISTSERV mail gets to the subscriber's inbox. To find the Deliverability Assessment, log into the LISTSERV 15.0 Web interface with your site administrator email address and password, and click on Server Administration > Site Configuration > Deliverability Assessment or visit: http://WWW_ARCHIVE_CGI?DELIV-DASHBOARD The Deliverability Assessment will ask for the DNS host name and IP address from which LISTSERV mail will be sent. If not automatically detected, enter the external DNS name and IP address of the LISTSERV server and press the "Submit" button.
The output screen will display LISTSERV's assessment of the server's deliverability, including any problems found and suggested resolutions. Tests that pass are represented with a green checkmark; those that fail are represented with a red exclamation point. Non-fatal errors and warnings are marked with a yellow exclamation point.
DomainKeys The first check is for a DomainKeys private and public key pair. Signing LISTSERV messages with DomainKeys is a means of providing verification for recipients that the purported sender of the message matches against a public key registered in DNS. (For more information on DomainKeys signing in LISTSERV, see the LISTSERV Tech Tip from LISTSERV at Work, Issue 3, 2006.) LISTSERV first checks for the existence of a private key as configured in LISTSERV's site configuration file. If found, it then checks the DNS record for the public key and verifies that the public and private keys match. Any problems with DomainKeys resolution will be highlighted in the Deliverability Assessment output. Failure to have a DomainKeys pair registered is not currently a major problem for most uses of LISTSERV. Few recipient sites are attributing high spam scores to unsigned messages at the time of this writing. However, DomainKeys signing (and thus checking of signatures) is becoming more prevalent. If you do choose to sign LISTSERV messages with DomainKeys, make sure that your signatures pass verification – a digital signature that appears to be forged is far worse than no signature at all. SPF/Sender ID The next set of checks is for SPF and Sender ID. Like DomainKeys, SPF and Sender ID provide a means by which to verify the identity of a message sender. Unlike DomainKeys, they rely on a DNS lookup on the sending server's IP address checked against a list of servers registered in DNS to send mail on behalf of the domain. (For more information on SPF and Sender ID, see the LISTSERV Tech Tip from LISTSERV at Work, Issue 3, 2006.) SPF checks that the originating IP address is authorized to send on behalf of the message envelope MAIL FROM; Sender ID also checks the message body From: and Sender: headers. You may register one or both types of records for your LISTSERV site. A soft (yellow) or hard (red) failure in both the SPF and Sender ID test is cause for some concern. While it doesn't necessarily mean that a large portion of email will be blocked by spam filters, there are many Internet sites that use SPF/Sender ID checks as one part of their spam scoring system. As with DomainKeys, it is better to have no SPF/Sender ID record at all than one that is misconfigured and causes your outbound email to look as if it were forged. DNS Records Finally, the Deliverability Assessment makes a number of DNS checks for both the LISTSERV hostname/IP address pair and those of the outbound SMTP server. The assessment reports on the status of the A (forward) records, the PTR (reverse) records and the MX (mail exchanger) records. Hard (red) failures in the DNS checks almost certainly mean that outbound email is already being blocked by some recipient sites. Many providers reject messages coming from a host without a proper DNS record. Soft (yellow) failures should be addressed but are of lesser concern. For example, it is not strictly required by Internet standards that the LISTSERV host name have a public MX record registered. However, some anti-spam systems do expect the MX record to be there, so it is advisable to have one in place, even if it points to the same host as the A record. While not an exhaustive resource for managing deliverability, the LISTSERV 15.0 Deliverability Assessment can assist in analyzing the basic technical building blocks of good delivery rates. It allows for other deliverability-enhancing policies (such as double opt-in, proactive reputation management, and maintaining good relationships with email service providers) to do their jobs, so that you can better do yours. |