CVE-2020-11022
Description
In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
https://nvd.nist.gov/vuln/detail/CVE-2020-11022
Some older versions of LISTSERV may be running with older versions of jQuery, primarily jQuery 3.3.1.
Mitigation
LISTSERV 17.5 ships with jQuery 3.7.1. If you are running an earlier version, you can upgrade to 17.5 which includes this update.
If you are running an older version of LISTSERV and are not in a position to upgrade to 17.5, you can download a newer version of jQuery and install it manually in the web archive directory.
1.Download a newer version of jQuery.
2.Unpack the newer version into the physical directory that maps to archives/js/ , e.g., so that the new version is in a new directory of its own. In this case, we are upgrading to jQuery 3.7.1:
E:\>dir listserv\www\archives\js
Volume in drive E is YOMI-E
Volume Serial Number is A006-A720
Directory of E:\listserv\www\archives\js
11/19/2024 19:47 <DIR> .
01/21/2025 14:00 <DIR> ..
11/19/2024 19:47 <DIR> chartjs
11/19/2024 19:47 <DIR> ckeditor
11/19/2024 19:47 <DIR> jquery
11/19/2024 19:47 <DIR> jquery-3.7.1
11/19/2024 19:47 <DIR> jquery-ui
11/19/2024 19:47 <DIR> jquery-ui-1.13.2
11/19/2024 19:47 <DIR> jscolor
11/19/2024 19:47 <DIR> tablesorter
11/19/2024 19:47 <DIR> tablesorter-2.31.3
0 File(s) 0 bytes
11 Dir(s) 37,303,136,256 bytes free
3.Update the JS-GLOBAL web template under Server Administration/Web Templates to use this version rather than the older version (this is set in the first line of the template).
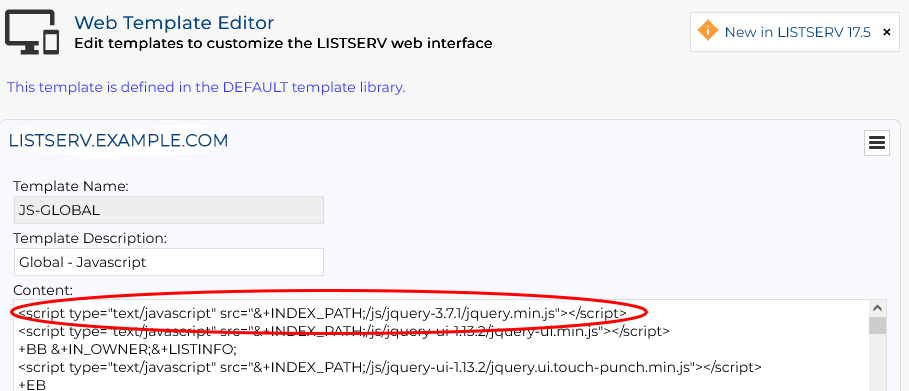
4.Finally, save the template and LISTSERV will start using the new jQuery version. At this point you may delete the original jquery directory, though this is not strictly required.
